

Custom Search
|
|

|
||
 MIL-HDBK-1013/1A
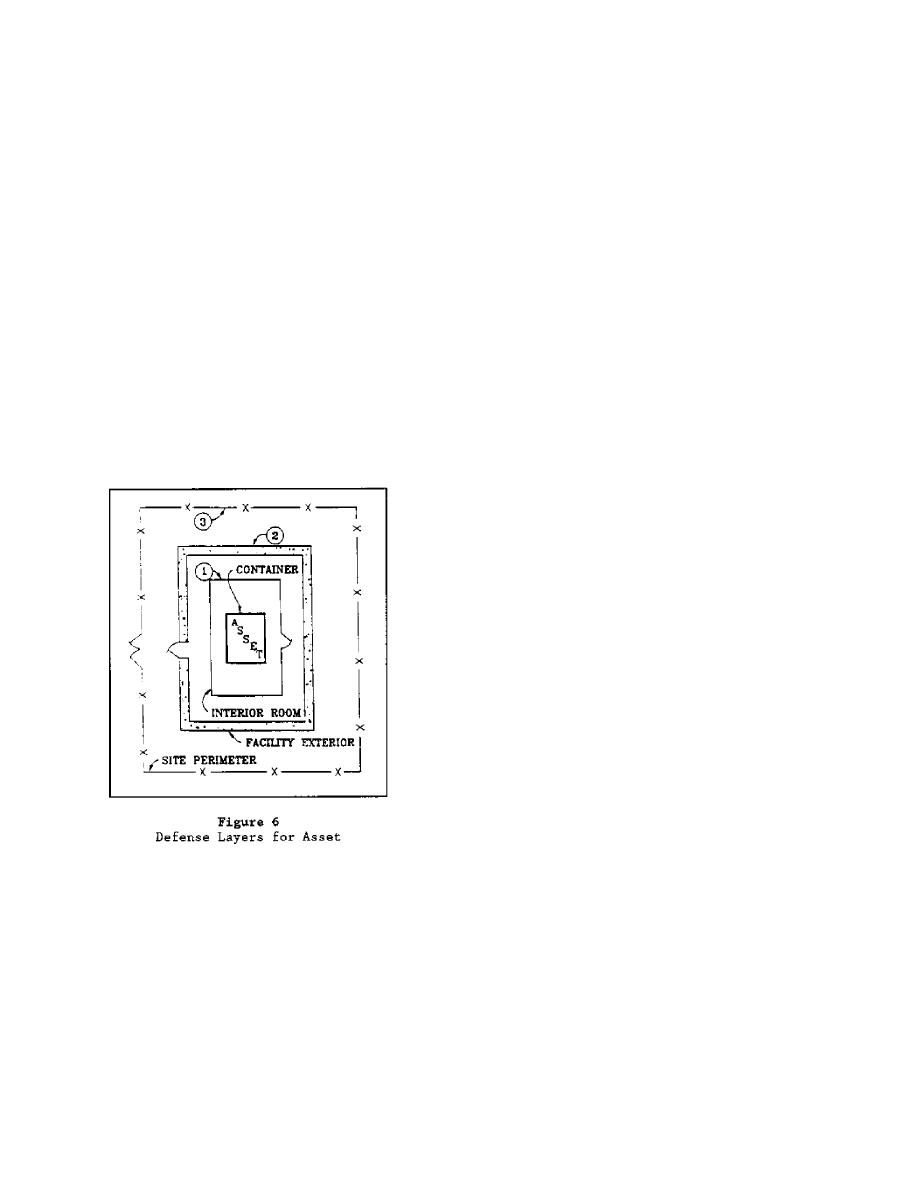
are encountered after detection. In general, the critical assets to be
protected should be located at a central point well within the interior of a
building presenting as many intermediate barriers to the intruder's path as
possible. An example of a building layout involving multiple barriers or
shells is illustrated in Figure 6. In general, the total delay time
associated with the site and building should equal the guard response time.
The total delay time, in turn, is the sum of the penetration times associated
with each barrier plus the intruder ingress/egress time between all barriers
where the timeline starts at the first point of intrusion detection. In this
regard, if the building is surrounded by a fence or other exterior
site-related barrier having an exterior intrusion detection system (IDS),
this can be considered the first layer of defense followed by the exterior of
the building and then any interior rooms, vaults, or containers housing the
asset. If there is no exterior fence IDS, the timeline can only start with
that barrier which immediately is preceded by a building interior IDS that
can detect the intruder. Finally, it is important to note that in order to
be effective, each component comprising a given shell (i.e., walls, roof,
floor, door, etc.) must offer an equivalent penetration delay time so as not
to create any weak links into the shell.
Figure 7 presents a graphic example of a
simple scenario for an
industrial-type facility which uses
conventional barriers. This example
illustrates how individual barrier penetration
times can be combined with
threat ingress times to establish total
intruder scenario times.
The scenario starts with the intruder just
outside the fenced area and ends
when the adversary has exited the fenced area
with the stolen material. In
this example, the adversary can accomplish the
theft in about 3 minutes, if
not interrupted by guards. Guards, of course,
will not be available to
interrupt the intruder unless he is detected
at some point in the scenario,
an alarm is sounded, and the guards have time
to respond.
To illustrate the guard response times needed
for various protection system
goals, assume that a fence perimeter detection system with an immediate alarm
capability exists at the fence in the example facility. If the goal is to
intercept the intruder before he can penetrate the building, the guards must
arrive within about 2 minutes of the alarm. If the goal is to intercept the
intruder before he can get his hands on the sensitive material (for possible
sabotage), the guards must arrive at that location within about 6 minutes of
27
|
 |
|
 |
||