

Custom Search
|
|

|
||
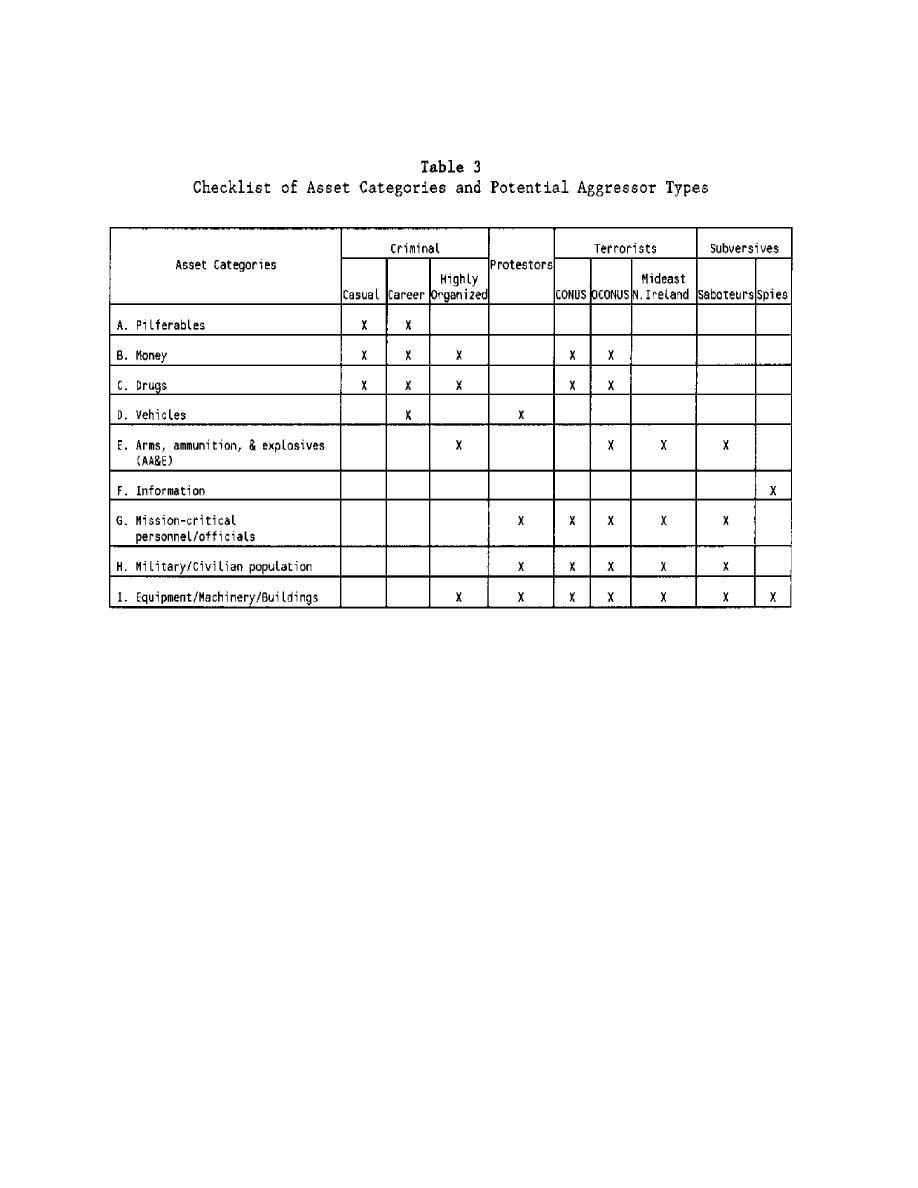 MIL-HDBK-1013/1A
such attacks.
2)
Intelligence sources are normally based on assessing the
likelihood of an attack and depend on whether: (a) aggressor types are in
the geographical area, (b) the aggressor's objective warrants the use of a
given attack at that severity level, and (c) the aggressor has access to the
required resources to carry through the attack.
3)
Threat accessibility to the required resources includes the
necessary: (a) equipment (attack tools, weapons, and supporting equipment);
(b) manpower (numbers and skill level); and (c) logistics required to carry
through the attack (i.e., the site and facility is directly accessible to the
aggressor and the skill, coordination, and timing required to carry through
the attack exist).
4)
Whether the attack is warranted by the objectives of the
threat (i.e., either personnel injury, asset destruction, theft, espionage,
or political embarrassment) depends upon whether a given objective is
relevant to the aggressor (considering the type of asset involved), and
whether the aggressor might be deterred by the protective measures at asset's
facility.
5)
Whether a given objective is attractive to an aggressor
depends, in turn, on whether: (a) the asset is perceived as valuable by the
aggressor (i.e., either because of its military criticality, high economic
value, or high political embarrassment impact); (b) the aggressor has reason
to believe
14
|
 |
|
 |
||