

Custom Search
|
|

|
||
 barriers, and sensor subsystems and their performance characteristics are
considered. Specific combinations are considered in terms of complementary
functions and supplementation of performance capabilities. For example,
intruder detection may be provided by point and space protection sensor
elements, or physical barriers may be used in conjunction with interior and
exterior detection sensors and area surveillance devices. The combinations
provide a synergistic effect in burdening the adversary by requiring special
equipment and by adding to penetration delay times. See DM-13.01 for
additional information regarding delay time considerations.
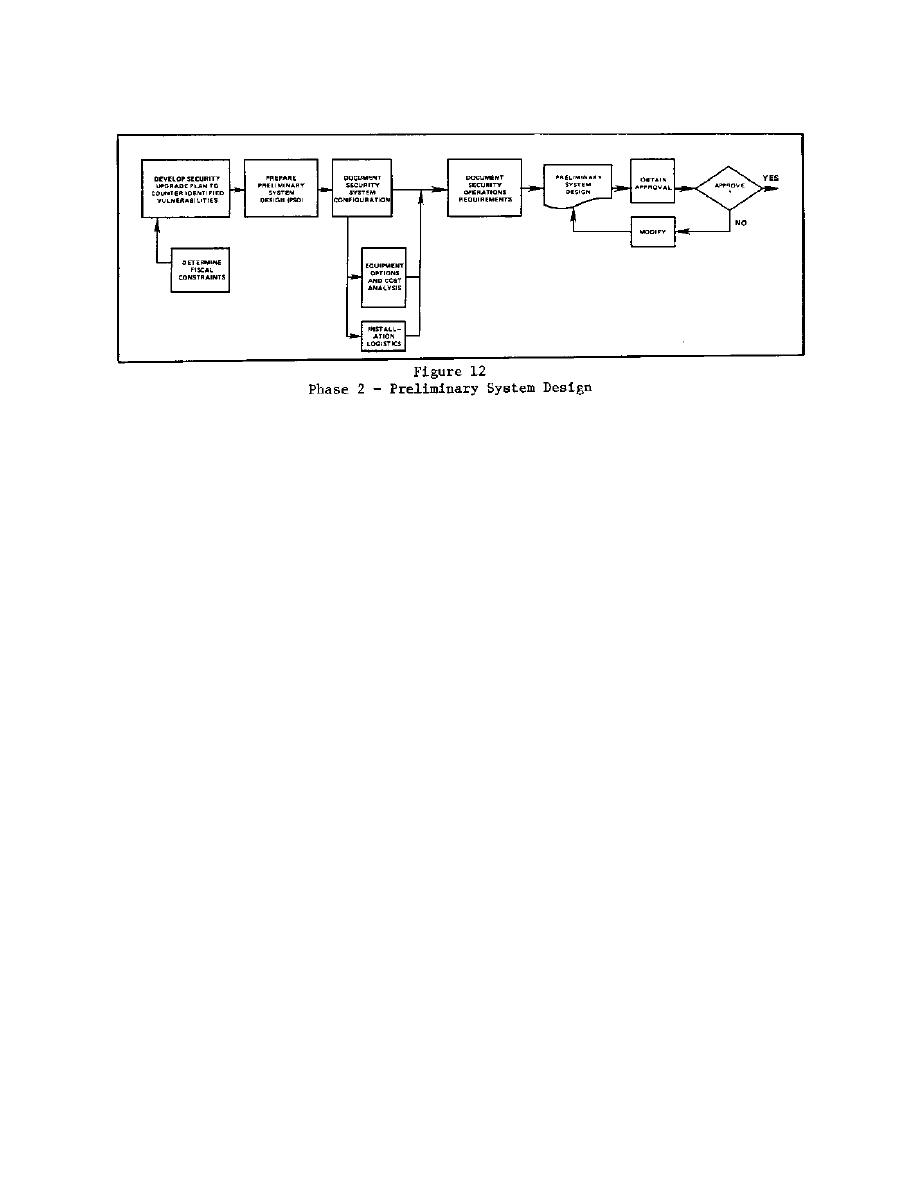
3.5.4.1.1 Determine Fiscal Constraints. Fiscal constraints are factored
into the equation early-on to provide pragmatic limits on design
alternatives. Security practitioners must devise a security upgrade plan in
consonance with these many constraints, and at the same time, reduce the
probability of successful adversary penetration. The results of the
consequences analysis and consensus steps in Phase 1 can directly serve the
interests of good judgment at this juncture.
3.5.4.1.2 Preliminary System Design (PSD). The conceptual design proceeds
to the preparation of a more definitive security system design. A system
configuration complete with identifiable subsystem and subsystem elements
can now be set forth. A variety of alternatives may still be available. For
example, if the design basis threat is an insider adversary in collusion
with outsiders, the mix of procedural, access control, and subsystem
redundancy features will still be under active debate. Hardware versus
personnel intensive solutions may look equally attractive during early
stages of PSD development depending upon threat and vulnerability
requirements. A principal set of considerations during intrusion detection
subsystem discussions will invariably surround the issues of nuisance alarms
and probabilities of detection of various electronic sensor configurations.
Site-unique environmental data generated during Phase 1 assessments will
provide specific input affecting the candidacy of various phenomenologies
and the site preparation required for potential applications. Design basis
threat data will directly assist in the determinations of operational
requirements for probability of detection success. In many cases, the use
of multiple and diverse sensor arrays, logically combined, in conjunction
|
 |
|
 |
||