

Custom Search
|
|

|
||
 MIL-HDBK-1013/12
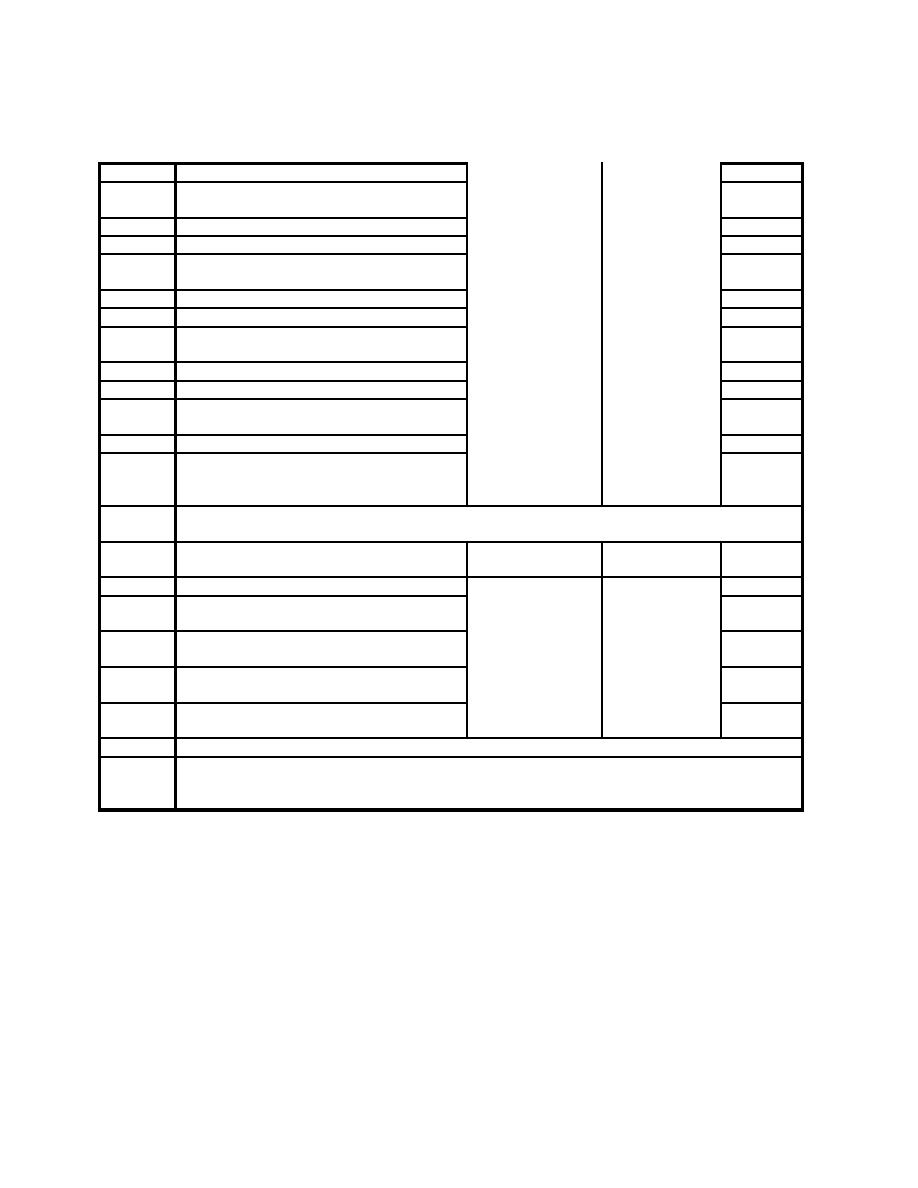
21
Transfer aggressors to worksheet.
and Severity
<2>
22
Indicate Applicable Tactics, use Figure
Levels
<3>
D-16.
23
For unsophisticated criminals:
<4>
24
For exterior tactic:
<5>
25
Check for severity level entry, use Figure
<6>
D-17. There is no entry.
26
Is there a severity level entry? No.
<7>
27
For ballistic tactic:
<4>
28
Check for severity level entry, use Figure
<6>
D-17. There is no entry.
29
Is there a severity level entry? No.
<7>
30
For forced entry tactic:
<4>
31
Check for severity level entry, use Figure
<6>
D-17. There is an entry.
32
Is there a severity level entry? Yes.
<7>
<8>
33
Determine appropriate threat severity
level, use Figure D-17. Threat severity
level is L. Enter L.
34
Repeat actions 24 through 33 for all remaining aggressors: sophisticated criminals,
organized criminal groups, and saboteurs.
35
Do Tactics Consolidation procedure.
Design Basis
Figure D-9
<5>
Threat
36
For exterior tactic:
Tactics
Figure D-18
<1>
37
Identify highest threat severity level: M
<2>
for medium.
38
Enter design basis threat severity level:
<3>
enter M.
39
Transfer threat severity level: enter M.
<4>
See Figure E-8
40
Determine design parameters, use Table
<5>
D-30: 50 lb. TNT.
41
Repeat actions 37 through 40 for all remaining tactics: ballistics and forced entry.
42
Repeat actions 3 through 41 for all remaining assets: office equipment, high-ranking
military personnel, administration staff and back up generator. See Figure E-9 through
Figure E-12.
240
|
 |
|
 |
||