

Custom Search
|
|

|
||
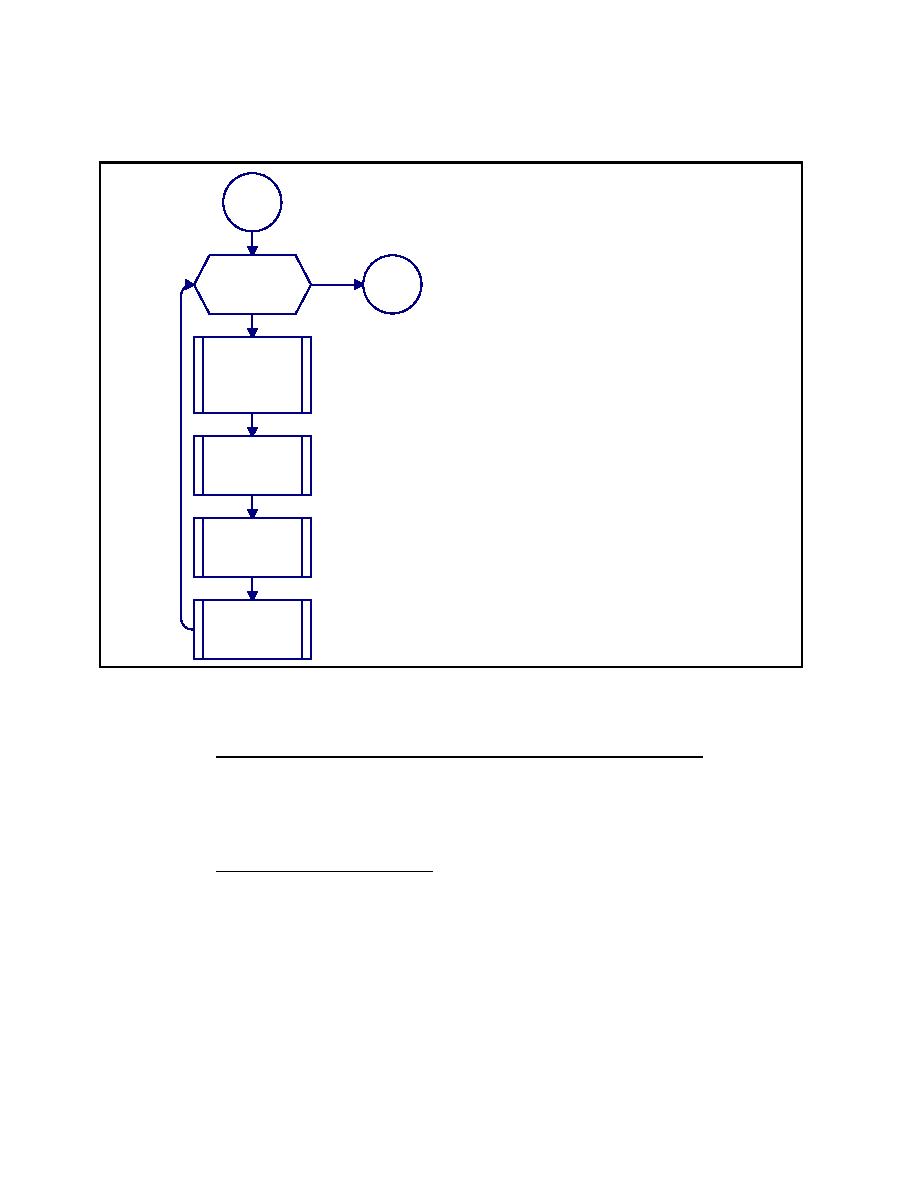 MIL-HDBK-1013/12
<1> For Each Asset. Loop through <2>,
<3>, and <4>, likelihood of aggression,
Start
applicable tactics and severity levels,
and tactics consolidation procedures
for each asset. After all assets have
been processed, return to Figure 1.
<2> Identification of Likely Aggressors.
<1> For Each
Done
Identify likely aggressors using
Stop
Asset
identification of likely aggressors
procedure presented in Figure D-10.
Next
Proceed to <3>
<3> Likelihood of Aggression. Determine
<2>
likelihood of aggression against asset
Identification of
using likelihood of aggression
Likely
procedure presented in Figure D-12.
Aggressors
Proceed to <4>.
<4> Applicable Tactics and Severity
Levels. Select tactics and severity
<3> Likelihood
levels for asset using applicable tactics
of Aggression
and severity levels procedure
presented in Figure D-14. Proceed to
<5>.
<5> Tactics Consolidation. Determine
<4> Applicable
worst severity level of each tactic using
Tactics and
tactics consolidation procedure
Severity Levels
presented in Figure D-18.
<5> Tactics
Consolidation
Figure D-9
Process Chart and Description: Design Basis Threat Procedure
D-3.3
Identification of Likely Aggressors Procedure. Figure
D-10 presents the process chart and procedure description for the
identification of likely aggressors procedure. It shows and
describes structures for identifying likely aggressors for
primary and secondary assets.
D-3.3.1
Required Information. The following information is
required for the identification of likely aggressors procedure:
a) Worksheets (see Appendix B):
1) Asset Value/Aggressor Likelihood (AVAL) for
both primary and secondary assets.
190
|
 |
|
 |
||